- Cisco Anyconnect Log In
- Cisco Anyconnect Vpn Client Download
- Fedora Cisco Anyconnect
- Cisco Anyconnect Windows 10 Download
OpenConnect is a cross-platform multi-protocol SSL VPN client which supports a number of VPN protocols:
Cisco AnyConnect VPN Client for Linux is used to establish secure connections for remote access in a Virtual Private Network. The Client supports all Cisco VPN access products and servers. In order to access the enterprise intranet remotely, we have to use the Cisco AnyConnect VPN client. We're allowed to install it on any personal machines, and they provide downloads and instructions for Windows, Mac and Linux. This works fine except for the routing table configurations they provide.
- Cisco AnyConnect (--protocol=anyconnect)
- Juniper SSL VPN (--protocol=nc)
- Pulse Connect Secure (--protocol=pulse
- Palo Alto Networks GlobalProtect SSL VPN (--protocol=gp)
- F5 Big-IP SSL VPN (--protocol=f5)
- Fortinet Fortigate SSL VPN (--protocol=fortinet)

OpenConnect is not officially supported by, or associated in any waywith Cisco Systems, Juniper Networks, Pulse Secure, Palo Alto Networks, F5,or Fortinet, or any of the companies whose protocols we may support in the future.It just happens to interoperate with their equipment. Trademarks belong totheir owners in a rather tautological and obvious fashion.
An openconnect VPN server (ocserv), which implementsan improved version of the Cisco AnyConnect protocol, has also beenwritten.
OpenConnect is released under the GNU Lesser Public License, version 2.1.
Motivation
Development of OpenConnect was started after a trial of the Cisco AnyConnectclient under Linux found it to have many deficiencies:
- Inability to use SSL certificates from a TPM or PKCS#11 smartcard, or even use a passphrase.
- Lack of support for Linux platforms other than i386.
- Lack of integration with NetworkManager on the Linux desktop.
- Lack of proper (RPM/DEB) packaging for Linux distributions.
- 'Stealth' use of libraries with dlopen(), even using the development-only symlinks such as libz.so — making it hard to properly discover the dependencies which proper packaging would have expressed
- Tempfile races allowing unprivileged users to trick it into overwriting arbitrary files, as root.
- Unable to run as an unprivileged user, which would have reduced the severity of the above bug.
- Inability to audit the source code for further such 'Security 101' bugs.
Naturally, OpenConnect addresses all of the above issues, and more.
New protocols
Adding new protocols to OpenConnect is relatively simple, andadditional protocols have been added over the years since usingOpenConnect allows a developer to concentrate on the protocol itselfand most of the boring details about platform-specific tunnel managementand IP configuration, and handling of client SSL certificates, are alreadyresolved.
If you have a protocol which you think it makes sense to support inOpenConnect, especially if you are able to help with interoperabilitytesting, please file an issuein GitLab.
Consistent multi-protocol support
Wherever possible, OpenConnect presents a uniform API and command-lineinterface to each of these VPNs. For example,openconnect --force-dpd=10will attempt dead peer detection every 10 seconds on every VPN thatsupports it, even though the actual mechanism used may be protocol-specific.Protocol-specific features and deficiencies are described on theindividual protocol pages.
The Cisco AnyConnect VPN client for Linux is recommended. The following instructions are provided for those who prefer to use a built-in VPN client for Linux.
Overview
Stanford's VPN allows you to connect to Stanford's network as if you were on campus, making access to restricted services possible.
Two types of VPN are available:
- Default Stanford (split-tunnel). When using Stanford's VPN from home, we generally recommend using the Default Stanford split-tunnel VPN. This routes and encrypts all traffic going to Stanford sites and systems through the Stanford network as if you were on campus. All non-Stanford traffic proceeds to its destination directly.
- Full Traffic (non-split-tunnel). This encrypts all internet traffic from your computer but may inadvertently block you from using resources on your local network, such as a networked printer at home. If you are traveling or using Wi-Fi in an untrusted location like a coffee shop or hotel, you may wish to encrypt all of your internet traffic through the Full Traffic non-split-tunnel VPN to provide an additional layer of security.
You can select thy type of VPN you want to use each time you connect to the Stanford VPN.
Install the OpenConnect client
Cisco Anyconnect Log In
- On Debian-compatible distributions (including Ubuntu), install the network-manager-openconnect-gnome package.
- On RedHat-compatible distributions (including Fedora and CentOS), install NetworkManager-openconnect-gnome.

Set up a new VPN interface
Cisco Anyconnect Vpn Client Download
- In System Settings, open the Network panel and click the + button to create a new interface.
- On Ubuntu, select VPN from the list of interface types and click Create.
- Select the Cisco AnyConnect Compatible VPN connection type (and, on Ubuntu, click Create).
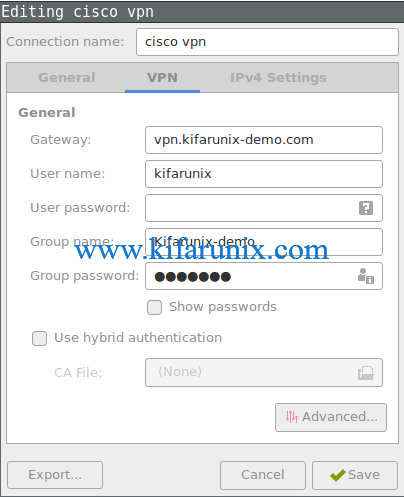
- Choose a name for the connection (e.g., Stanford) and set the Gateway to su-vpn.stanford.edu. Then, click Add (or Save).
Fedora Cisco Anyconnect
Connect to the Stanford VPN
Cisco Anyconnect Windows 10 Download
- In the Network panel, turn the new interface on.
- On Ubuntu, in the System menu you may also click the Network icon select the new interface from the list of VPN Connections.
- On Fedora, in the System menu you may choose VPN Off and click Connect.
- In the Connect to VPN dialog box, enter the following information and then click Login.
- GROUP: select Default Stanford split- tunnel or Full Traffic non-split-tunnel
- Username: your SUNet ID
- Password: your SUNet ID password
Complete the two-step authentication.
